Here's a quick summary of what you need to know, but make sure to read on to find out exactly what has been changing and the impact it's had.
- Yes, 100% always use an SSL (Secure Sockets Layer) regardless of what the browser looks like.
- Do you really need an Extended Validation (EV) SSL? Probably not (Google doesn’t even use one).
- Ask your website team if you can tighten the cipher support to reduce attack vectors.
Browser flags
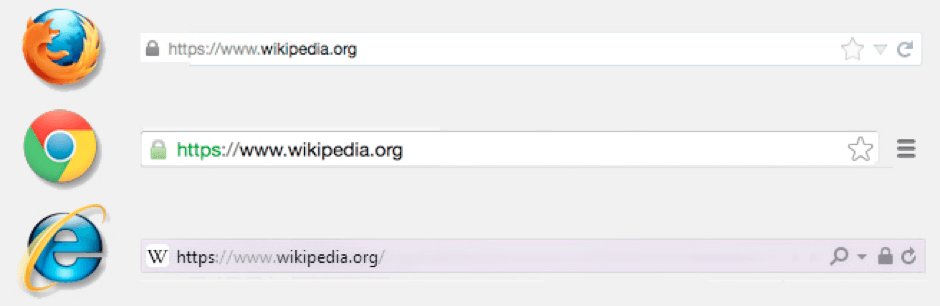
In our last article, we showed you some easy ways to know that a website you’re visiting is using an encrypted connection, it looked like this:
Things have changed slightly since Google said that because installing an SSL is so easy, a user should not be reminded each time that they’re secure.
That being said, Google Chrome will no longer display a bright green badge in the user's browser, letting them know that the website you’re viewing is secure.
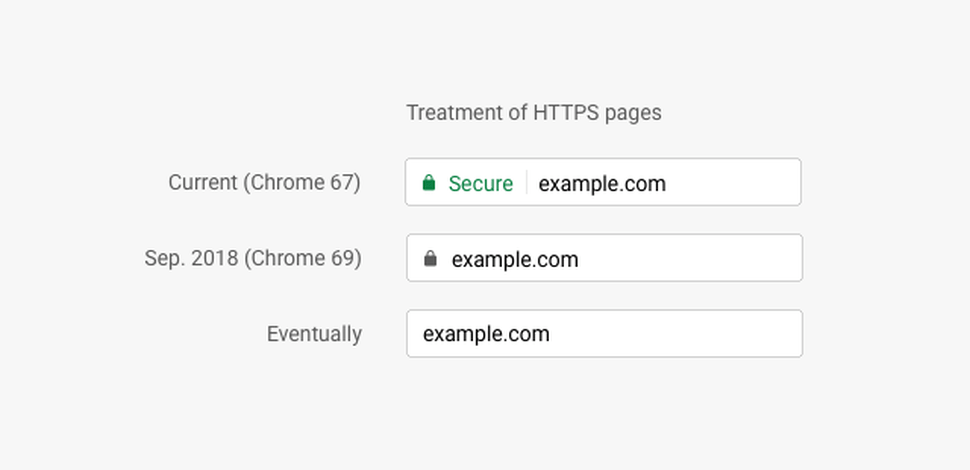
You will however still get the little padlock icon, it’s just not as obvious - the same goes for users of Safari.
In complete contrast to this, Firefox has now acquired the green padlock.
Below, Selesti have created a visual guide which allows you to see what a URL looks like in each browser, with and without SSL. We will keep this regularly updated.
Bookmark this page to keep up to date
How banks killed the EV SSL (sort of)
For a long time now, there’s been a version of an SSL called “Extended Validation” or “EV”.
Historically, anybody can buy and install an SSL. However, to get an EV SSL, you must go through a manual step with real humans, to confirm you are who you say you are and that you have the authority to purchase that SSL.
The most common use for this is financial institutes and email services like Hotmail. This is to reduce phishing, where someone might make a fake website to look like your bank, using a similar website address e.g. www.halfax-online.co.uk (notice the misspelling. You might then try to login with your personal details. However, instead of logging in, it will save and send off their login credentials to a hacker.
So, to combat this EV SSLs would allow you to prove that the website address the user is on, is in fact genuine. It would look something like:

This means the user can be confident that the website address they’re on is their bank.
You might think this sounds like a no-brainer and everybody should be doing this. Well, you're right. However, some large organisations have complicated the situation. They want to save money and advertise their parent brand, so you end up in situations like this:

So the EV SSL is listed as “Lloyds Banking Group” however the website is “Bank of Scotland"
Okay, as an informed customer you might know they’re owned by the same group, however, think of other instances, where an obscure holding company own the SSL, but the website or domain is completely different?

This isn’t much help to the user. If the EV SSL is meant to represent the website you’re visiting, if it doesn’t clearly correspond to the website they are visiting, then how useful is it? Where do we draw the line?
SSL ciphers
As the years go by and computers become more powerful, we come up with faster and stronger encryption methods. This is a good thing.
You’re able to tighten your security on your websites by using the latest ciphers as modern browsers and computers can handle them.
So what’s the catch? Well, in order to really tighten the security, you’re meant to disable old ciphers to make sure anything that’s previously been cracked by hackers cannot be used against you. The problem then comes with older systems trying to engage with your website.
It’s becoming more common for "hacking farms", where masses of low paid workers using old exploitable technology, are scouring the internet for exploits to sell on the black market. So, by upgrading your security and only using modern ciphers, you’re able to protect yourself against a wide variety of problems.
Problems occur when businesses that have not been able to upgrade their software, e.g. the NHS, are forced to use insecure software like Internet Explorer. Remember the recent NHS hacking?
If you know that you have a large userbase using Internet Explorer 11, you can check which ciphers they support on SSL Labs.
By upgrading, you’re blocking these users from accessing your website. Most of the time, this is normally found in underfunded enterprise tier companies who do not invest in their IT infrastructure.
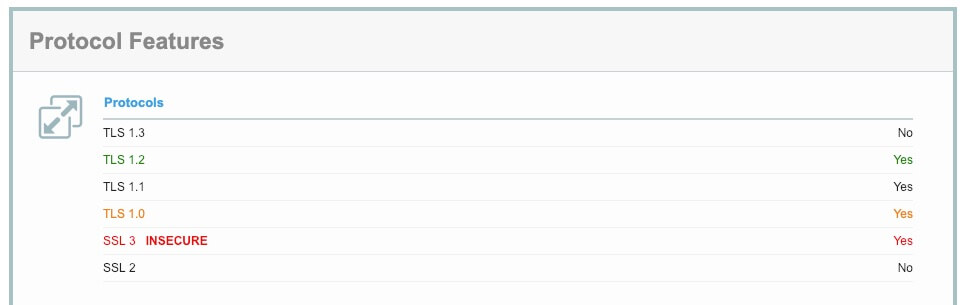
We can see from the image above that IE11 does not support the latest TLS 1.3, which means that once it’s fully released, your users will not be able to benefit from this level of encryption.
Additionally, you’re also excluding certain online services from working with you. For example, the payment gateway Realex Payments still only supports old ciphers. This means that in order to increase the security of your website for your users and everybody else, you need to make certain decisions about who you partner with.
Can you really afford to work with companies who are unable to provide yourself and your customers a secure environment?
If you have any questions about SSL, cybersecurity or just fancy a chat please email us at hello@selesti.com, we love to help!